WHY GLOBAL SUPPLY CHAIN GROUP?
Because Safe, Secure, And, Profitable Supply Chains Are Even More Mission Critical Today. And, no other firm knows supply chains like we do.
If you talk to us, we can tell you objectively about the entire competitive landscape of the supply chain consulting industry and how we fit into it. After all, we pioneered supply chain consulting in Australia and maybe even the world.
Please do not ask our opinion about other consulting firms you might be considering. We do not like to say bad things about our competitors, and every one of them has its place under the sun.
WHY GLOBAL SUPPLY CHAIN GROUP?
Because Safe, Secure, And, Profitable Supply Chains Are Even More Mission Critical Today. And, no other firm knows supply chains like we do.
If you talk to us, we can tell you objectively about the entire competitive landscape of the supply chain consulting industry and how we fit into it. After all, we pioneered supply chain consulting in Australia and, maybe, even in the world.
We do not like to say bad things about our competitors on our website or anywhere else, so please do not ask our opinion about other consulting firms you might be considering.
WHAT DOES GLOBAL SUPPLY CHAIN GROUP STAND FOR?
Our Mission, Vision and Values have empowered us over the past 22 years of our business. They form the core of what we stand for. Contact us to know more about these.
MISSION
mission
Your profits are under constant attack from your suppliers, competitors, customers and many other directions.
Our mission is to identify and defend weak links in the supply chain, and leverage the strong links to maximise profitability over extended periods of time.
VISION
Vision
VALUES
Values
@ We work as a single team with the clients.
@ We respect our clients and expect the same from them.
@ We leave when the project is done.
@ We do what is necessary to deliver supply chain results.
@ We tell the truth, nicely.
@ We keep learning and teaching supply chain.







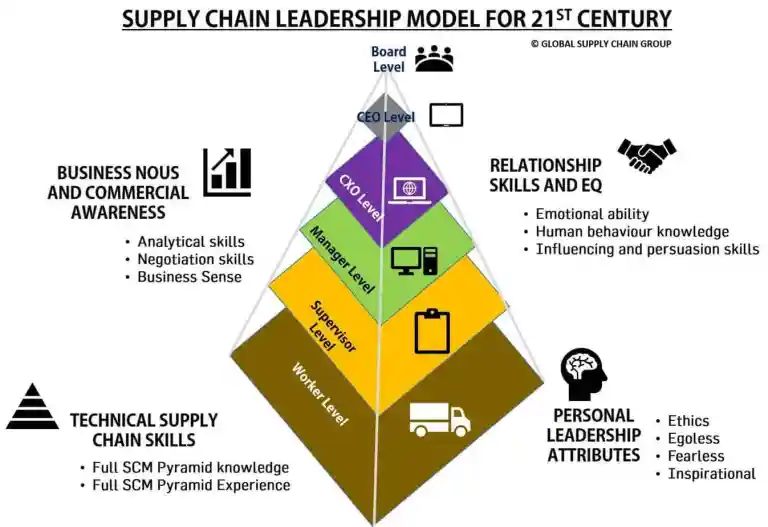
WHY DOES GLOBAL SUPPLY CHAIN GROUP ACHIEVE BETTER RESULTS AT LOWER COSTS?
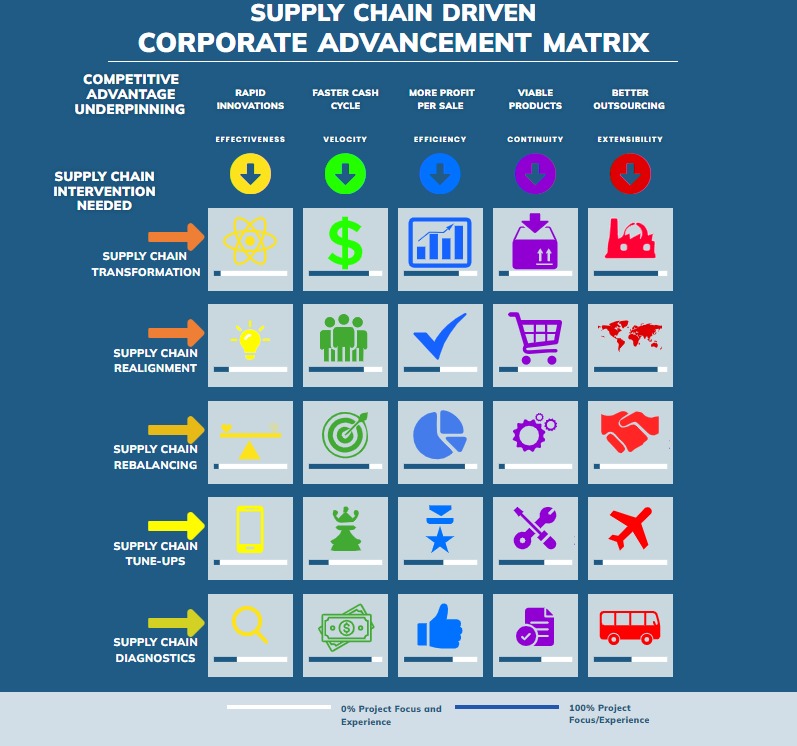
Because our highly experienced supply chain strategy experts focus significantly on your company's UNIQUE system dynamics.
Get in touch with us to see how we consistently use the following proprietary matrix to pinpoint the exact nature of systems dynamics:
COMPETITIVE ADVANTAGE UNDERPINNING
SUPPLY CHAIN INTERVENTION NEEDED
SUPPLY CHAIN TRANSFORMATION
SUPPLY CHAIN REALIGNMENT
SUPPLY CHAIN REBALANCING
SUPPLY CHAIN TUNE-UPS
SUPPLY CHAIN DIAGNOSTICS
PRINCIPAL FLOW OF SUPPLY CHAIN
RAPID INNOVATION
EFFECTIVENESS
FLOW OF INFORMATION
FASTER CASH CYCLE
VELOCITY
FLOW OF MONEY
MORE PROFIT PER SALE
EFFICIENCY
FLOW OF PRODUCT
PRODUCT CYCLE (NPD)
CONTINUITY
FLOW OF RISK
BETTER OUTSOURCING
EXTENSIBILITY
FLOW OF VALUE
0% Project Project Focus Experience
100% Project Project Focus Experience
Uniquely among consulting companies, it aids in just the right intervention at the right place (rather than trying to boil the ocean to make a cup of tea).
SUPPLY CHAIN CASE STUDIES - GET RESULTS, NOT EXCUSES
With more than 27 years of "pure" supply chain strategy experience, original thinking, and the contribution of the "inventor of supply chain management" on our team, you will see results, instead of a three-act circus that your past consulting firms showed you.
GLOBAL SUPPLY CHAIN STRATEGY EXPERTISE
THE FIRST AND, Still The Best SUPPLY CHAIN STRATEGY CONSULTANTS IN THE WORLD.
There are few firms with a consistent track record since January 2000 of successful large scale supply chain strategy projects. For supply chain strategy projects, measured against MBBB firms and their clones, Global Supply Chain Group’s key differentiation is that today, we achieve better results with smaller teams.
Here are some key statistics for the last 22 Years Since Our Inception On 11 January 2000:
Supply Chain STRATEGY BlogS
Supply Chain Governance For Chairpersons and Boards
Total articles - 16
Last update - 21 December 2022
LEAD ARTICLE THIS MONTH:
Importance of KPI in Supply Chain- Try these tricks!
Supply Chain Transformation For CEO’s
Total articles - 40
Last update - 22 December 2022
LEAD ARTICLE THIS MONTH:
Coming Re-Alignment Of The Natural Gas Supply Chains On A Global Scale
Supply Chain For CXO’s and VP’s
Total articles - 24
Last update - 21 December 2022
LEAD ARTICLE THIS MONTH:
The Right Way To Improve Your Supply Chain?
Business Strategy and Supply Chain
Total articles - 155
Last update - 16 December 2022
LEAD ARTICLE THIS MONTH:
Change Your Processes Before Implementing New Software
Supply Chain Driven Business Transformation
Total articles - 102
Last update - 21 December 2022
LEAD ARTICLE THIS MONTH:
The Business Boosters- The Shocking Revelation of 5 Star
Supply Chain Execution
Total articles - 21
Last update - 21 December 2022
LEAD ARTICLE THIS MONTH:
Airlines Are Adjusting Their 5-STAR Business Networks To The New Economic Reality
Supply Chain and Inventory Optimisation
Total articles - 42
Last update - 20 December 2022
LEAD ARTICLE THIS MONTH:
Sustainable Packaging Industry And Its History
Supply Chain Digitization
Total articles - 34
Last update - 21 December 2022
LEAD ARTICLE THIS MONTH:
Assign Clear Personal Responsibility For Each Cost Line To A Single Individual of Supply Chain Business
Supply Chain Strategy
Total articles - 61
Last update - 22 December 2022
LEAD ARTICLE THIS MONTH:
A Re-Thinking Supply Chains Approach By stuart Emmett
Supply Chain Management
Total articles - 126
Last update - 22 December 2022
LEAD ARTICLE THIS MONTH:
Supply Chain Leadership in Tough Time
Supply Chain Security
Total articles - 27
Last update - 22 December 2022
LEAD ARTICLE THIS MONTH:
Apple’s Business Network Conundrum Dump Samsung Or Not?
Green Supply Chain And CSR
Total articles - 26
Last update - 20 December 2022
LEAD ARTICLE THIS MONTH:
Benefits Of Global Supply Chain and adds Value?
Logistics, Freight Management, and Supply Chain
Total articles - 49
Last update - 20 December 2022
LEAD ARTICLE THIS MONTH:
Australia Leads The Way To Globalisation With Triple FTA With Asia’s Big Three
Global Supply Chain News
Total articles - 60
Last update - 20 December 2022
LEAD ARTICLE THIS MONTH:
New Business Models For The New World
Global Supply Chain Group Helps Business Leaders Succeed
Supply Chain Case Studies
Global Supply Chain shipping Case study
Total articles - 18
Last update - 10 March 2023
LEAD CASE STUDIES THIS MONTH:
Unlocking Efficiency: Achieving Bulk Supply Chain Savings And Streamlined Operations With Improved Safety Stock And Transportation
Increased cost savings, Efficient Supply Chain Case Study
Total articles - 20
Last update - 10 March 2023
LEAD CASE STUDIES THIS MONTH:
Maximizing Engagement Strategy For Product Users Through Contract Manufacturing
Linear Programming Model and supply chain case study
Total articles - 09
Last update - 10 March 2023
LEAD CASE STUDIES THIS MONTH:
Linear Programming Model Leads To $2.3 Million Annual Savings In Delivery Costs: Analysis
Supply chain Boosting Efficiency and Transportation Case Study
Total articles - 22
Last update - 10 March 2023
LEAD ARTICLE THIS MONTH:
Boosting Efficiency And Cutting Costs In Coal Transport: A Peer Group Comparison
Supply Chain business transformation Case Study
Total articles - 20
Last update - 10 March 2023
LEAD CASE STUDIES THIS MONTH:
Transforming Aircraft Overhaul: Strategies For Optimizing Business Performance
Supply Chain Costs Saving case study
Total articles - 22
Last update - 10 March 2023
LEAD CASE STUDIES THIS MONTH:
Unlocking Efficiency: Achieving Bulk Supply Chain Savings And Streamlined Operations With Improved Safety Stock And Transportation
Supply Chain Distribution challenges case study
Total articles - 10
Last update - 10 March 2023
LEAD CASE STUDIES THIS MONTH:
Streamlining Insurance Settlements Through Supply Chain Segmentation And Value Vs Complexity Quadrant
Supply Chain Freight Optimization case study
Total articles - 22
Last update - 10 March 2023
LEAD ARTICLE THIS MONTH:
Optimizing Global Manufacturing Footprint: A Comprehensive Approach To Production, Logistics, Distribution, And Supply Chain Management
Supply Chain Greenfield Plant Case Study
Total articles - 09
Last update - 10 March 2023
LEAD CASE STUDIES THIS MONTH:
Transforming Aircraft Overhaul: Strategies For Optimizing Business Performance
supply chain Inventory Management case study
Total articles - 21
Last update - 10 March 2023
LEAD CASE STUDIES THIS MONTH:
Managing Critical Supply Chain Risks: A Comprehensive Guide To Risk Rating Tables
Global supply chain Clients feedback
What Do People who matter Say About Us?







P & L Executive

Coats Group plc

Credence Logistics
The focus of this Website
Foremost, the focus is on you, your supply chains, and, the improvement projects on top of your mind.
This website is not meant to tell you about our stellar achievements in the past 22 years of running this company. Nor do we want to focus here on how we predicted well in advance the shipping and supply chain crises currently gripping the world.
The focus is firmly on you, your supply chains, the improvement projects on top of your mind at the moment, and what role we could play in those projects for you to achieve better results in the shortest time frame.
In our observations of the past thirty years, no supply chain starts as dysfunctional. Most supply chains were reasonably functional at some time in the past.
Why are Supply Chain problems continuing to gather momentum?
As improvements and additions are tacked on to them and, as the technology progresses, as the competitors move, and as mergers, acquisitions, divestitures and other corporate strategy moves are executed, most supply chains become increasingly dysfunctional.
Can anyone predict these problems with any certainty? How can you solve the most significant current issues hurting your supply chain? How can you trace the root cause of what is damaging your supply chain the most?
Sometimes, the root cause can hide very far from the problem itself.
Your team may need our help to investigate the full extent of your supply chain problems and all the complications the root cause could be causing far and wide. Your supply chain-driven issues could be more visible in sales, marketing, finance, your supplier base, and your customer base.
The critical question is this:
How can you balance coherent, holistic Supply Chain thinking with fast, focused action?
Get in touch with us to discuss how our clients have done it every time over the last two decades or more.
five questions to ask before seeking supply chain consultants
What will a great supply chain for your company look like?
You do not need a supply chain strategy consultant if you already have a precise answer to this question, and, you can answer the rest of the four questions easily and accurately.
However, as in most cases, the answer is somewhat vague like a scatter gun shot, you need to start at the top. Clarify and agree on this answer before you do anything else.
You may need a firm like ours to help you clarify answers to these questions, and many similar questions. Contact us on [email protected] in that case.
What kind of supply chain problems do you have?
If it is a strategic problem, a tactical consultant simply would not be able to get their minds around it. They will likely ignore the real problem, or trivialise it, and make themselves look useful by focusing on the wrong problems that they can comprehend.
Same applies to the areas of supply chain that are directly underperforming. Shipping, manufacturing, warehousing, logistics, inventory experts can rarely step out of their respective comfort zones. Very few of them can deal with the real board level strategic supply chain projects.
Similarly many board level strategy consultants rarely know even the terminology used by the lower level personnel in supply chains – they end up ‘inventing’ their own terminology, which creates adverse reactions, and, proves counterproductive in most cases.
Is it a supply chain governance problem, or a supply chain management problem?
Supply chain management deals with problem solving in supply chain, while supply chain governance deals with problem prevention in supply chains. Most companies now pay a lot of attention to supply chain management, but pay scant attention to supply chain governance. And, as a result they end up employing the wrong kind of consultants at the wront time.
What is the current level of supply chain maturity in your company?
Supply chain is all about integration, and optimisation. On a scale of 0-10 try and assess the level of integration and optimisation in your company. At a lower levels of integration and optimisation, you need to assess your company’s comfort level with higher level concepts such as integration, or optimisation. Do not waste your money on super-expensive strategic consultants if you, and your team, are not yet ready to move to a higher level of supply chain. That would be like buying Ferrari to drive on a dirt road.
Is the problem really in the supply chain, or is the supply chain being make a scapegoat for problems elsewhere in the company?
It is common knowledge that everyone complains about the supply chain in almost every company. All sorts of ills are blamed on supply chain management simply because, in general, the supply chain leaders are the least savvy in boardroom politics.
While this is a big weakness (and must be addressed as such), bigger weaknesesses in sales, marketing or even finance can be masked by just pointing their collective fingers at the supply chain team. If that is also the case in your company, you are wasting your effort by focusing your transformational effort solely on supply chain management.
More Questions?
It is only natural to have many other questions in a situation like this. Afterall, your company is as unique as you are. Every situation has its own nuances.
The best way to move forward is to attain clarity by a quick chat with us.
Click to arrange a quick Tele-call
Book your zoom below: